Intro To Cyber
Lecture 6
Date Taken: Fall 2025
Status: Completed
Reference: LSU Professor Joseph Khoury, ChatGPT
Encryption Continuation
The Key Pair
In asymmetric encryption, a key pair consists of a public key and a private key.
Key generation, build both the public and priavate keys at the same time.
It is based on complex mathematical algorithms that ensure the keys are mathematically related yet distinct.
The security of the system relies on the mathematical relationship between the two keys, making it computationally infeasible to derive the private key from the public key.
Everyone can have the public key, but only the owner has the private key.
Key Escrow
Key escrow is a security mechanism where cryptographic keys are stored by a trusted third party, known as the escrow agent.
This allows authorized entities to access encrypted data under specific circumstances, such as legal requirements or organizational policies.
Key escrow can be used in various scenarios, including:
- Data Recovery: In case of lost or forgotten keys, authorized personnel can retrieve the keys from the escrow agent to access encrypted data.
- Law Enforcement Access: Governments may require key escrow to allow law enforcement agencies to access encrypted communications during investigations, subject to legal oversight.
- Organizational Policies: Companies may implement key escrow to ensure that critical data can be accessed by designated personnel in case of emergencies or employee turnover.
Encrypting Stored Data
Encrypting stored data, also known as data at rest encryption, involves using cryptographic techniques to protect data that is stored on physical media, such as hard drives, solid-state drives, or cloud storage.
The goal is to ensure that even if the storage medium is compromised, the data remains unreadable without the appropriate decryption key.
Common methods for encrypting stored data include:
- Full Disk Encryption (FDE): Encrypts the entire storage device, including the operating system and all files. Examples include BitLocker (Windows) and FileVault (macOS).
- File-Level Encryption: Encrypts individual files or folders, allowing for more granular control over which data is protected. Examples include EFS (Encrypting File System) on Windows.
- Database Encryption: Encrypts data within databases to protect sensitive information, such as customer records or financial data. Examples include Transparent Data Encryption (TDE) for SQL Server and Oracle databases.
- Cloud Storage Encryption: Encrypts data stored in cloud services, either by the cloud provider or by the user before uploading. Examples include AWS KMS and Azure Key Vault.
Database Encryption
Database encryption involves using cryptographic techniques to protect sensitive data stored within a database.
The goal is to ensure that even if the database is compromised, the data remains unreadable without the appropriate decryption key.
Common methods for database encryption include:
- Transparent Data Encryption (TDE): Encrypts the entire database at the file level, ensuring that data is automatically encrypted when written to disk and decrypted when read. Examples include TDE for SQL Server and Oracle databases.
- Column-Level Encryption: Encrypts specific columns within a database table, allowing for more granular control over which data is protected. This method is useful for protecting sensitive information, such as credit card numbers or social security numbers.
- Application-Level Encryption: Encrypts data before it is stored in the database, providing end-to-end encryption. This method ensures that data remains encrypted throughout its lifecycle, even when processed by the application.
- Key Management: Proper key management practices are essential for database encryption, including secure key generation, storage, rotation, and access control to ensure that only authorized users can decrypt the data.
Transport Encryption
Transport encryption, also known as data in transit encryption, involves using cryptographic techniques to protect data as it is transmitted over networks.
The goal is to ensure that even if the data is intercepted during transmission, it remains unreadable without the appropriate decryption key.
Common methods for transport encryption include:
- SSL/TLS (Secure Sockets Layer/Transport Layer Security): Protocols that provide secure communication over the internet by encrypting data between web browsers and servers. TLS is the successor to SSL and is widely used for securing websites (HTTPS).
- VPN (Virtual Private Network): Creates a secure, encrypted tunnel for data transmission over public networks, allowing remote users to access private networks securely. Examples include IPsec and OpenVPN.
- SSH (Secure Shell): A protocol that provides secure remote access to systems and secure file transfers by encrypting the communication between the client and server.
- Email Encryption: Techniques such as S/MIME (Secure/Multipurpose Internet Mail Extensions) and PGP (Pretty Good Privacy) that encrypt email messages to protect their content during transmission.
Key Lengths
Key length refers to the size of the cryptographic key used in encryption algorithms.
It is typically measured in bits and plays a crucial role in determining the security level of the encryption.
Longer keys provide stronger security, as they increase the number of possible key combinations, making it more difficult for attackers to perform brute-force attacks.
Key Stretching
Key stretching is a technique used to enhance the security of weak or short cryptographic keys by increasing their effective length.
This is typically done by applying a computationally intensive algorithm to the original key, making it more resistant to brute-force attacks.
Key Exchange
Key exchange is the process of securely sharing cryptographic keys between parties to enable encrypted communication.
The goal is to ensure that only the intended recipients can access the keys, preventing unauthorized access.
Common key exchange methods include:
Encryption Technology
Encryption technology encompasses various methods and tools used to secure data through cryptographic techniques.
It plays a crucial role in protecting sensitive information from unauthorized access and ensuring data integrity and confidentiality.
Encryption technologies include:
- Trusted Platform Module (TPM) - A hardware-based security module that provides secure key storage, cryptographic operations, and platform integrity verification. TPMs are commonly used in computers and mobile devices to enhance security. Cryptography processor and secure storage for cryptographic keys. Also password protected meaning no dictioanry attacks.
- Hardware Security Module (HSM) - A dedicated hardware device that provides secure key management and cryptographic operations. HSMs are used in enterprise environments to protect sensitive data and ensure compliance with security regulations.
- Key Management System (KMS) - A system for managing cryptographic keys, including their generation, storage, distribution, and revocation. KMS solutions help organizations maintain control over their encryption keys and ensure compliance with security policies.
- Secure Enclave - A secure area within a processor that provides isolated execution and secure storage for sensitive data and cryptographic keys. Secure enclaves are commonly used in mobile devices and modern processors to enhance security. Provides extensive security features, example, has it own boot ROM, memory, and crypto engine. Isolated from the rest of the system.
Hasing and Digital Signatures
- Hashes - Hashing turns data into a short code that can't be reversed. It's used to store passwords safely, check file integrity, and verify identity with digital signatures.
- Collision - A collision happens when two different inputs create the same hash. Hash functions turn any-size data into a fixed-size code, but they should always be unique. MD5 is known for collisions, so it's not safe for important use.
- Pratical Hashing - Use hashing to check downloads by comparing the file's hash with the one provided. For passwords, store a salted hash instead of the actual password, so even the system doesn't know your real password.
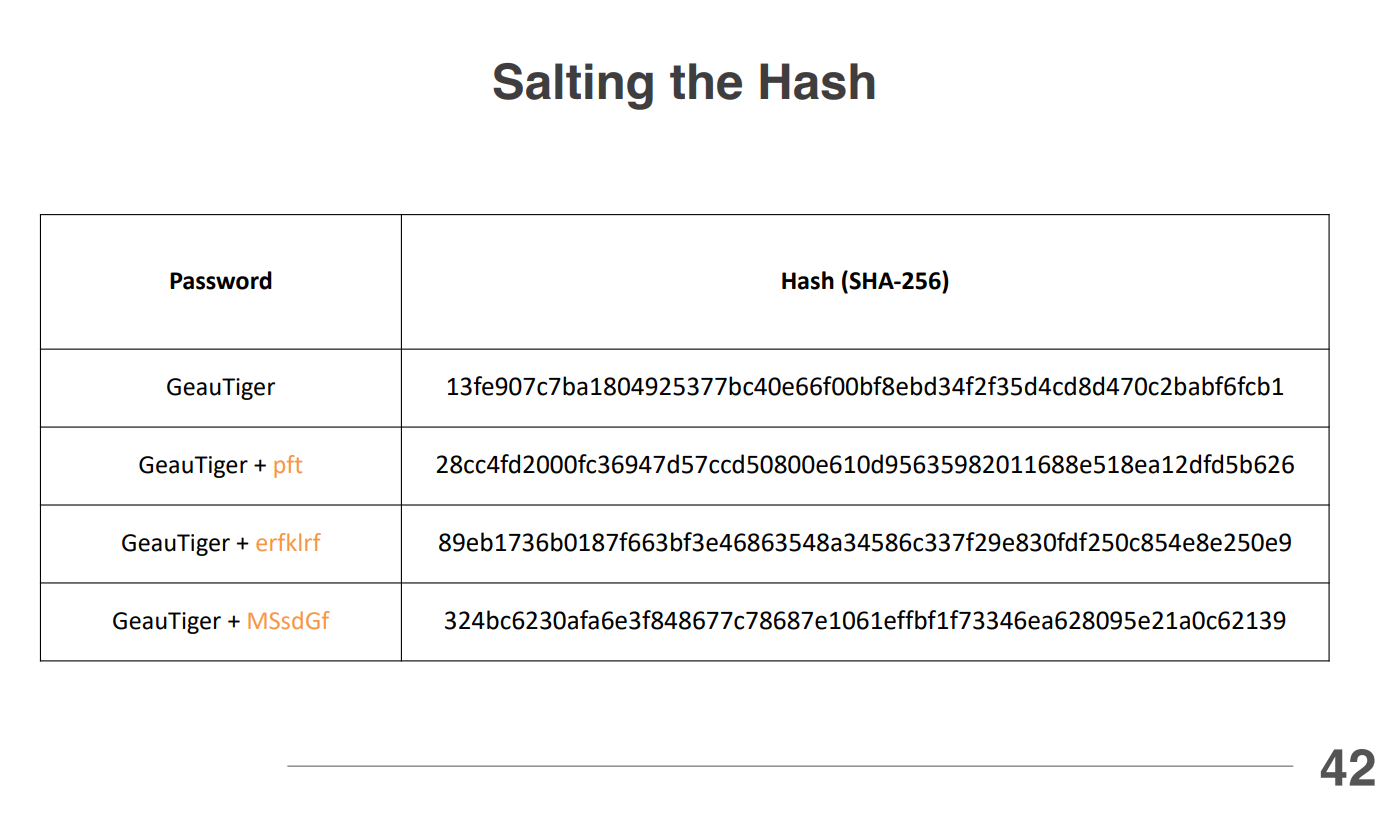
- Salting - A salt is random data added to each password before hashing. Every user gets a unique salt, which is stored with the password. This makes rainbow tables useless and slows down brute-force attacks, though it doesn't completely prevent them.
Digital Signatures
Digital signatures are a way to prove that a message or document is authentic and hasn't been changed.
They use a combination of hashing and asymmetric encryption to create a unique signature that can be verified by anyone with the sender's public key.
The process of creating and verifying a digital signature involves several steps:
Digital Certificates
Digital certificates are electronic documents that prove the ownership of a public key.
They are issued by trusted entities called Certificate Authorities (CAs) and contain information about the certificate holder, their public key, and the CA's digital signature.
Digital certificates are used to establish trust in online communications, such as secure websites (HTTPS), email encryption, and code signing.
Certificate Authorities
Certificate Authorities (CAs) are trusted entities that issue and manage digital certificates.
They play a crucial role in establishing trust in online communications by verifying the identity of certificate requesters before issuing certificates.
Third-Party Certificate Authorities
Third-party Certificate Authorities (CAs) are independent organizations that issue digital certificates to individuals, organizations, and devices.
They play a crucial role in establishing trust in online communications by verifying the identity of certificate requesters and ensuring the authenticity of their public keys.
Certificate Signing Requests
A Certificate Signing Request (CSR) is a block of encoded text that is submitted to a Certificate Authority (CA) when applying for a digital certificate.
The CSR contains information about the entity requesting the certificate, including their public key and other identifying details.
To create a CSR, the requester typically uses a tool or software that generates the key pair and the CSR.
The private key is kept secret and secure by the requester, while the CSR is sent to the CA for processing.
Once the CA verifies the information in the CSR and the requester's identity, it issues a digital certificate that includes the public key and other relevant details.
Private Certificate Authorities
Private Certificate Authorities (CAs) are organizations or entities that operate their own CA infrastructure to issue and manage digital certificates for internal use within an organization.
Private CAs are typically used in enterprise environments where there is a need for secure communication and authentication among internal systems, applications, and users.
However, private CAs also come with challenges, such as the need for proper key management, ensuring the security of the CA infrastructure, and maintaining trust within the organization.
It is essential to implement robust security practices and policies to mitigate risks associated with operating a private CA.
Self-SIgned Certificates
Self-signed certificates are digital certificates that are signed by the same entity that created them, rather than being issued by a trusted Certificate Authority (CA).
They are typically used for internal testing, development environments, or in situations where trust can be established without relying on an external CA.
Wildcard Certificates
Wildcard certificates are digital certificates that can secure multiple subdomains of a primary domain using a single certificate.
They are identified by an asterisk (*) in the domain name, which represents any subdomain.
For example, a wildcard certificate for *.example.com can secure subdomains such as www.example.com, mail.example.com, and blog.example.com.
Key Revocation
Key revocation is the process of invalidating a cryptographic key before its scheduled expiration date.
This is typically done when a key is compromised, lost, or no longer needed, to prevent unauthorized access to encrypted data or systems.
Key revocation can be performed for both symmetric and asymmetric keys, and it is an essential aspect of key management in cryptographic systems.
- Certificate Revocation Lists (CRLs): A list of revoked digital certificates published by a Certificate Authority (CA). Clients can check the CRL to determine if a certificate is still valid before trusting it.
- Online Certificate Status Protocol (OCSP): A protocol that allows clients to query a CA in real-time to check the revocation status of a specific certificate. OCSP provides a more efficient and timely method for checking certificate validity compared to CRLs.
- Key Expiration: Setting an expiration date for keys and certificates ensures that they are automatically invalidated after a certain period, reducing the risk of long-term exposure if a key is compromised.
- Key Rotation: Regularly replacing cryptographic keys with new ones helps minimize the impact of key compromise and enhances overall security.
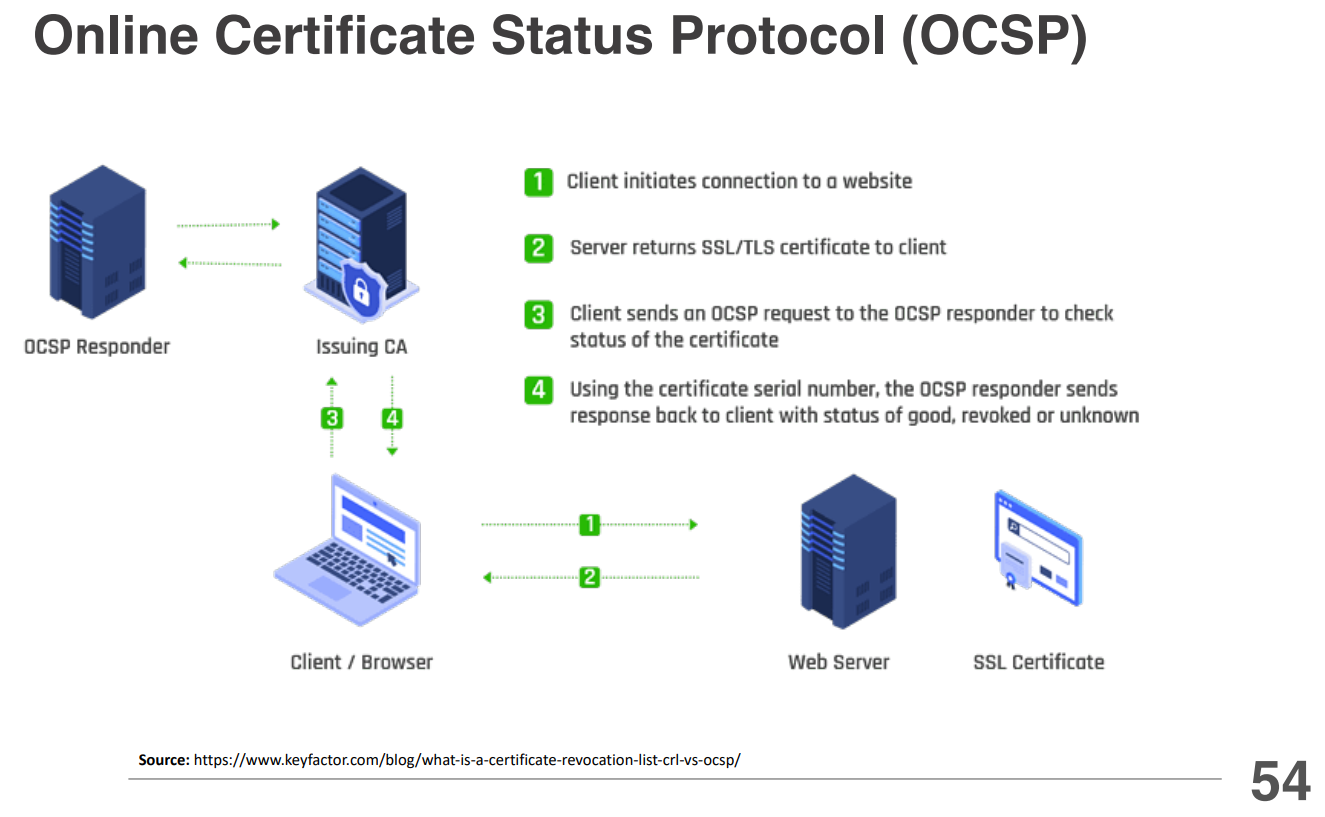
Online Certificate Status Protocol (OCSP)
The Online Certificate Status Protocol (OCSP) is a protocol used to check the revocation status of digital certificates in real-time.
It provides a more efficient and timely method for verifying the validity of a certificate compared to traditional methods, such as Certificate Revocation Lists (CRLs).
The OCSP process involves several steps:
- Client Request: When a client (such as a web browser) encounters a digital certificate, it sends an OCSP request to the OCSP responder specified in the certificate. The request includes the serial number of the certificate being checked.
- OCSP Responder: The OCSP responder is a server operated by the Certificate Authority (CA) that issued the certificate. It receives the OCSP request and checks its database to determine the revocation status of the requested certificate.
- Response Generation: The OCSP responder generates an OCSP response, which indicates whether the certificate is "good" (valid), "revoked" (invalid), or "unknown" (not found in the database). The response is digitally signed by the OCSP responder to ensure its authenticity.
- Client Verification: The client receives the OCSP response and verifies the digital signature to ensure that it came from a trusted OCSP responder. Based on the revocation status provided in the response, the client decides whether to trust the certificate or not.