Intro To Cyber
Lecture 7
Date Taken: Fall 2025
Status: Completed
Reference: LSU Professor Joseph Khoury, ChatGPT
Threats
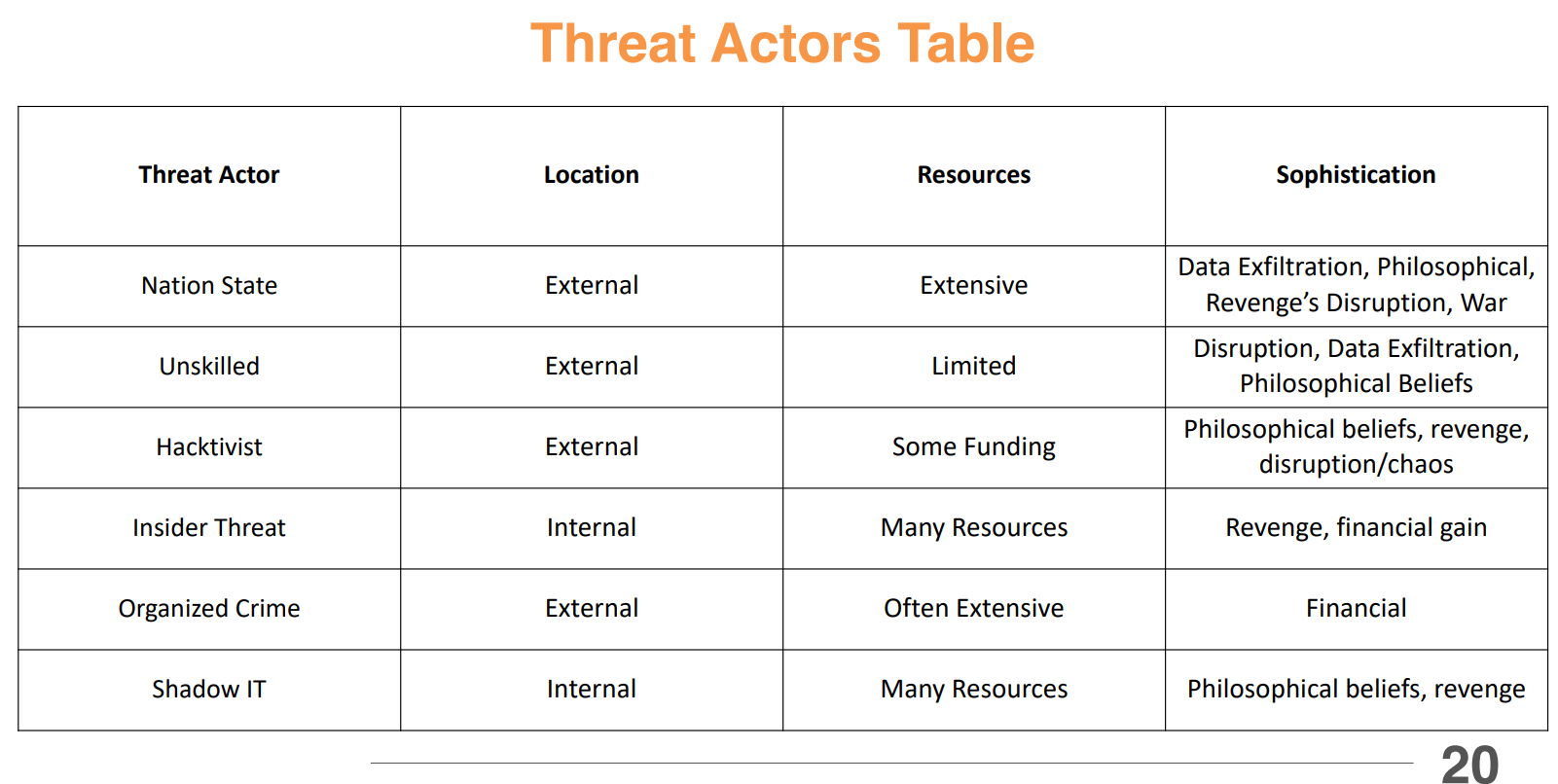
Threat Actors
Threat actors are individuals or groups that pose a risk to the security of information systems and data.
They can have various motivations, capabilities, and methods of attack. Common types of threat actors include:
- Hackers: Individuals or groups who exploit vulnerabilities in systems for various reasons, such as financial gain, political motives, or personal challenge. They can be categorized into white-hat (ethical hackers), black-hat (malicious hackers), and gray-hat (hackers who operate in a legal gray area).
- Insiders: Employees, contractors, or other individuals with authorized access to an organization's systems who may intentionally or unintentionally compromise security. Insider threats can include data theft, sabotage, or accidental data leaks.
- Nation-State Actors: Government-sponsored groups that conduct cyber espionage, cyber warfare, or other cyber operations to advance national interests. They often have significant resources and capabilities.
- Cybercriminals: Organized groups or individuals who engage in illegal activities for financial gain, such as ransomware attacks, phishing scams, and identity theft.
- Hacktivists: Individuals or groups who use hacking techniques to promote political or social causes. Their actions may include defacing websites, leaking sensitive information, or disrupting services.
- Script Kiddies: Inexperienced individuals who use pre-written scripts or tools to launch attacks without a deep understanding of the underlying technology. They often seek notoriety rather than financial gain.
Motications of Threat Actor
Threat actors can have various motivations for their actions, which can influence the methods they use and the targets they choose. Common motivations include:
- Financial Gain: Many threat actors are motivated by the potential for monetary profit. This can include activities such as ransomware attacks, data theft, and fraud.
- Political or Ideological Goals: Some threat actors, such as hacktivists or nation-state actors, are driven by political or ideological beliefs. They may target organizations or governments to promote their cause or disrupt opposing entities.
- Espionage: Nation-state actors and some cybercriminals may engage in cyber espionage to gather sensitive information for strategic advantage, whether for economic, military, or political purposes.
- Revenge or Personal Grievance: Insiders or disgruntled employees may be motivated by personal grievances against their employer or colleagues, leading them to sabotage systems or leak sensitive information.
- Curiosity or Challenge: Some hackers, particularly white-hat and gray-hat hackers, may be motivated by a desire to test their skills and challenge themselves against complex systems.
- Notoriety: Certain threat actors, such as script kiddies, may seek recognition and fame within the hacking community by carrying out high-profile attacks.
Nations States
Nation-state actors are government-sponsored groups that conduct cyber operations to advance national interests.
They often have significant resources, capabilities, and expertise, allowing them to carry out sophisticated attacks against various targets.
Highest sophistication and resources. Often part of a country's military or intelligence services. Goals include espionage, disruption, and propaganda.
Unskilled Attackers
Unskilled attackers, often referred to as "script kiddies," are individuals who lack advanced technical skills but use pre-written scripts or tools to launch cyber attacks.
They typically seek notoriety or personal satisfaction rather than financial gain or political objectives.
They often use tools developed by others to exploit known vulnerabilities. Their attacks can still cause significant damage, especially if they target unpatched systems.
Hacktivists
Hacktivists are individuals or groups who use hacking techniques to promote political or social causes.
Their actions may include defacing websites, leaking sensitive information, or disrupting services to draw attention to their cause.
They often target organizations or governments they perceive as unjust or corrupt. Their methods can include website defacements, DDoS attacks, and data leaks.
Insiders
Insiders are individuals with authorized access to an organization's systems who may intentionally or unintentionally compromise security.
Insider threats can include data theft, sabotage, or accidental data leaks, and they can be particularly challenging to detect and prevent.
They can be current or former employees, contractors, or business partners. Insider threats can be malicious (intentional harm) or unintentional (accidental data leaks).
Organized Crime
Organized crime groups are structured criminal organizations that engage in illegal activities for financial gain.
In the context of cybersecurity, these groups often conduct cybercrime operations such as ransomware attacks, data breaches, and fraud.
They operate with a high level of organization and coordination, often involving multiple individuals with specialized roles. Their activities can include ransomware, phishing, identity theft, and financial fraud.
Shadow IT
Shadow IT refers to the use of information technology systems, software, and services within an organization without the knowledge or approval of the IT department.
This can include the use of unauthorized applications, cloud services, or devices that may pose security risks.
Common examples include employees using personal cloud storage services, messaging apps, or software tools that are not sanctioned by the organization. Shadow IT can lead to data breaches, compliance violations, and other security issues.
Threat Vector
A threat vector is the path or method used by a threat actor to gain unauthorized access to a system or network.
Understanding threat vectors is crucial for developing effective security measures and protecting against potential attacks.
Common threat vectors include:
- Message-Based - Phishing emails, malicious attachments, and social engineering tactics that trick users into revealing sensitive information or downloading malware.
- Image-Based - Malicious images or graphics that exploit vulnerabilities in image processing software to deliver malware or execute code. Some significant security concerns with image based attacks is HTML injection and Javascript attack code. Browsers must provide input validation to advoid running malicious code.
- File-Based - Infected files, such as documents or executables, that contain malware or exploit vulnerabilities when opened or executed. Adobe PDF, Zip/RAR files (or any compression type), Microsoft Office.
- Voice Call - Vishing (voice phishing) attacks that use phone calls to impersonate legitimate entities and trick individuals into revealing sensitive information or performing actions that compromise security. Spam over Internet Protocol (SPIT) is a form of vishing that uses VoIP technology to deliver unsolicited calls or messages. War dialing is a technique used to identify vulnerable systems by automatically dialing a range of phone numbers to find modems or fax machines that can be exploited and it is still being used today. Call tampering is the manipulation of caller ID information to disguise the true origin of a call, often used in vishing attacks to appear as a trusted source.
- Removable Device - USB drives, external hard drives, and other removable media that can introduce malware or unauthorized access when connected to a system. Examples include USB flash drives, external hard drives, and memory cards. They can be used to transfer malware or steal sensitive data.
- Vulnerable Software - Exploiting known vulnerabilities in software applications, operating systems, or network devices to gain unauthorized access or execute malicious code. Examples include unpatched software, outdated operating systems, and misconfigured network devices.
- Unsupported Systems - Using systems or software that are no longer supported by the vendor, which may lack security updates and patches, making them vulnerable to attacks. Examples include legacy systems, end-of-life software, and unsupported operating systems.
- Insecure Systems - Systems that lack proper security measures, such as firewalls, antivirus software, or encryption, making them susceptible to attacks. Examples include systems with weak passwords, open ports, and unencrypted communications.
Open Service Ports
Open service ports are network ports that are actively listening for incoming connections and are accessible from external networks.
While open ports are necessary for certain services to function, they can also pose security risks if not properly managed and secured.
Most network-based services connect over a TCP or UDP port.
Common open service ports include:
- HTTP (Port 80): Used for unencrypted web traffic. It is essential to secure web applications running on this port to prevent attacks such as cross-site scripting (XSS) and SQL injection.
- HTTPS (Port 443): Used for encrypted web traffic. While HTTPS provides a secure communication channel, it is still important to ensure that web applications are properly configured and free from vulnerabilities.
- FTP (Port 21): Used for file transfers. FTP is inherently insecure, as it transmits data in plaintext. It is recommended to use secure alternatives such as SFTP or FTPS.
- SSH (Port 22): Used for secure remote access. While SSH provides strong encryption, it is important to implement additional security measures, such as key-based authentication and limiting access to trusted IP addresses.
- SMTP (Port 25): Used for sending email. Open SMTP ports can be exploited for spam distribution and email spoofing. It is important to configure email servers securely and implement anti-spam measures.
- DNS (Port 53): Used for domain name resolution. Open DNS ports can be targeted for DNS amplification attacks. It is important to secure DNS servers and restrict access to authorized users.
- RDP (Port 3389): Used for remote desktop access. Open RDP ports can be targeted for brute-force attacks and unauthorized access. It is recommended to use VPNs or other secure methods for remote access.
Default Credentials
Default credentials refer to the pre-configured usernames and passwords that come with hardware devices, software applications, or network equipment.
These credentials are often set by the manufacturer and are intended to be changed by the user during the initial setup process.
Default credentials pose a significant security risk if they are not changed, as they are widely known and can be easily exploited by attackers to gain unauthorized access to systems and networks.
Very easy to find the defaults for your access point or router. https://www.routerpasswords.com is a good resource to find default passwords.
Supply Chain Vectors
Supply chain vectors refer to the various points of vulnerability within the supply chain that can be exploited by threat actors to compromise the security of products, services, or data.
These vulnerabilities can arise at any stage of the supply chain, from raw material sourcing to manufacturing, distribution, and delivery.
Common supply chain vectors include:
- Third-Party Vendors: Suppliers, contractors, or service providers that have access to an organization's systems or data can introduce vulnerabilities if they do not follow proper security practices.
- Software Dependencies: The use of third-party libraries, frameworks, or components in software development can introduce vulnerabilities if these dependencies are not regularly updated and patched.
- Hardware Components: The inclusion of compromised or counterfeit hardware components in devices can lead to security breaches and unauthorized access.
- Logistics and Transportation: The physical movement of goods and materials can be targeted by threat actors to intercept or tamper with products during transit.
- Insider Threats: Employees or contractors within the supply chain who have access to sensitive information or systems may intentionally or unintentionally compromise security.
Phishing
Phishing is a cyber attack technique that involves sending fraudulent messages, often via email, that appear to come from a reputable source.
The goal of phishing is to trick recipients into revealing sensitive information, such as login credentials, financial information, or personal data, or to download malware onto their devices.
Common types of phishing attacks include:
- Email Phishing: The most common form of phishing, where attackers send emails that appear to be from legitimate organizations, such as banks or online services, to lure recipients into clicking on malicious links or attachments.
- Spear Phishing: A targeted form of phishing that focuses on specific individuals or organizations. Attackers often gather personal information about their targets to create more convincing and personalized messages.
- Whaling: A type of spear phishing that targets high-profile individuals, such as executives or government officials, with the goal of stealing sensitive information or gaining access to critical systems.
- Smishing: Phishing attacks that use SMS (text messages) to deliver fraudulent messages and links to mobile devices.
- Vishing: Phishing attacks that use voice calls to impersonate legitimate entities and trick individuals into revealing sensitive information or performing actions that compromise security.
Business Email Compromise
Business Email Compromise (BEC) is a type of cyber attack that targets organizations by compromising legitimate business email accounts.
The goal of BEC attacks is to trick employees, customers, or partners into transferring funds, revealing sensitive information, or performing other actions that benefit the attacker.
BEC attacks often involve social engineering tactics, such as impersonating a high-level executive or a trusted vendor, to create a sense of urgency and legitimacy.
Tricks and Misdirections
Tricks and misdirections are techniques used by threat actors to deceive individuals and manipulate their behavior in order to achieve malicious objectives.
These tactics often involve exploiting human psychology and cognitive biases to create a sense of urgency, trust, or fear.
Some tricks are typosquatting - a type of cybersquatting where attackers register domain names that are similar to legitimate ones, often by making slight misspellings or variations, an example - https://Isu.edu.
Pretexting - creating a fabricated scenario to engage a target and extract information or perform actions. An example is pretending to be from IT support to gain access to a system.
Impersonation
Impersonation is a technique used by threat actors to deceive individuals by pretending to be someone they are not.
The goal of impersonation is to gain trust and manipulate the target into revealing sensitive information, performing actions, or granting access to systems or resources.
Eliciting Information
Eliciting information is a technique used by threat actors to extract sensitive or confidential information from individuals through various means, often by exploiting human psychology and social engineering tactics.
The goal of eliciting information is to gather data that can be used for malicious purposes, such as identity theft, fraud, or unauthorized access to systems.
Identity Fraud
Identity fraud is the unauthorized use of another person's personal information, such as their name, social security number, or financial details, to commit fraud or other crimes.
Identity fraud can have serious consequences for victims, including financial loss, damage to credit scores, and legal issues.
Protect Against Impersonation
To protect against impersonation attacks, individuals and organizations can implement several strategies:
- Verify Identities: Always verify the identity of individuals requesting sensitive information or access to systems. Use multiple methods of verification, such as phone calls or in-person meetings, to confirm their legitimacy.
- Educate Employees: Provide regular training and awareness programs to educate employees about impersonation tactics and how to recognize and respond to potential threats.
- Implement Strong Authentication: Use multi-factor authentication (MFA) to add an extra layer of security for accessing sensitive systems and data. This can help prevent unauthorized access even if credentials are compromised.
- Monitor Communications: Implement monitoring tools to detect unusual or suspicious communications, such as emails or phone calls, that may indicate an impersonation attempt.
- Establish Clear Policies: Develop and enforce clear policies regarding the handling of sensitive information and access requests. Ensure that employees understand the importance of following these policies.
- Use Technology Solutions: Utilize email filtering, anti-phishing tools, and other security technologies to help identify and block potential impersonation attempts.
Watering Hole Attack
A watering hole attack is a cyber attack technique where threat actors compromise a website or online resource that is frequently visited by a specific group of individuals or organizations.
The goal of the attack is to infect the targeted users' devices with malware or gain unauthorized access to their systems when they visit the compromised site.
The term "watering hole" is derived from the idea of predators waiting at a watering hole to ambush prey, as attackers wait for their targets to visit the compromised site.
Executing the Watering Hole Attack
The execution of a watering hole attack typically involves several steps:
- Target Selection: The attacker identifies a specific group of individuals or organizations they want to target, often based on their industry, location, or interests.
- Website Compromise: The attacker identifies a website or online resource that is frequently visited by the target group and exploits vulnerabilities in the site to gain control over it. This may involve injecting malicious code, exploiting software vulnerabilities, or using social engineering tactics to gain access.
- Malware Deployment: Once the website is compromised, the attacker injects malware into the site, which may include drive-by downloads, exploit kits, or other malicious payloads designed to infect visitors' devices.
- Target Infection: When members of the target group visit the compromised website, their devices may become infected with the malware, allowing the attacker to gain unauthorized access to their systems, steal sensitive information, or perform other malicious actions.
- Post-Infection Activities: After successfully infecting the target devices, the attacker may use various techniques to maintain persistence, exfiltrate data, or move laterally within the target's network.
Watering Hole Attack Defense
Some defense measures if defense-in-depth in which you have multiple layers of security so if one layer is compromised you have another layer to fall back on.
Firewalls and IPS stops the network traffic before things get worse.
Anti-virus/Anti-malware signature updates to help detect known malware.
Web content filtering to block access to known malicious sites.
Regular patching and updates to fix vulnerabilities in software and systems.
User education and awareness training to help users recognize and avoid potential threats.
Misinformation/Disinformation
Misinformation and disinformation are two related but distinct concepts that involve the spread of false or misleading information.
Misinformation refers to the unintentional spread of false information, while disinformation refers to the deliberate creation and dissemination of false information with the intent to deceive or manipulate.
Both misinformation and disinformation can have significant impacts on individuals, organizations, and society as a whole, particularly in the context of social media and online communication.
Brand Immpersonation
Brand impersonation is a type of cyber attack where threat actors create fake websites, social media profiles, or other online resources that mimic legitimate brands or organizations.
The goal of brand impersonation is to deceive individuals into believing they are interacting with the legitimate brand, often to steal sensitive information, distribute malware, or conduct fraud.